Trying out Tailscale
2022-12-20

Tailscale is a VPN service that makes the devices and applications you own accessible anywhere in the world, securely and effortlessly. It enables encrypted point-to-point connections using the open source WireGuard protocol, which means only devices on your private network can communicate with each other.
Creating an account is very easy, the options to sign up are exclusively SSO as tailscale is not an identity provider. You can use your existing account (Google, Github, AzureAD etc) so utilising your identity providers existing security features (2FA/MFA) which will then apply to tailscale access.
Each time you register a new machine/device to your private network it will appear under the Machines tab within your account. This private network is known as a tailnet which assigns each machine its own private ipv4 and ipv6 address, its important to note these private addresses will always stay the same for that machine/device on your network.
Once you have created an account, you can then begin to install tailscale to add machines to your accounts tailnet and view them on your admin console.
I ran the install script for tailscale on a linux server, as well as installing it onto my latptop and my android phone.
curl -fsSL https://tailscale.com/install.sh | sh
On the linux server I then enabled tailscale SSH on the servers:
sudo tailscale up --ssh
With Tailscale SSH, you can:
- SSH as normal, using Tailscale for authentication. With Tailscale SSH, Tailscale takes over port 22 for SSH connections incoming from the Tailscale network. Tailscale will authenticate and encrypt the connection over WireGuard, using Tailscale node keys. The SSH client and server will still create an encrypted SSH connection, but it will not be further authenticated.
- Verify high-risk connections with check mode. Optionally require certain connections, or connections as certain users (e.g., root), to re-authenticate before connecting. This allows the user to access these high-risk applications for the next 12 hours or for a specified check period before re-authenticating again.
I now have a remote linux server and my phone and laptop appearing under my machines on the admin console.
By default each machine/device that is added to your network will be auto-assigned a name based on OS hostname. This can be updated so the machine/device is something more mnemonic. This also means via magicdns you can use the name instead of the IP address.
On my phone after registering it, I enabled tailscale by launching the android app:

To enable tailscale SSH access from my phone and laptop to those servers I updated the access controls of the tailnet policy file via the admin console.
All rules eventually boil down to allowing traffic from a particular source IP address to a destination IP address and port. While you can write rules that reference IP addresses directly, it's more common to use higher-level specifiers like usernames and groups, which Tailscale automatically translates to the right low-level rules.
Update the SSH sections and tagOwners sections in the tailnet policy file, which will allow tailscale SSH access from my laptop or phone to the server using tags:
"ssh": [
{
"action": "accept",
"src": ["tag:phone", "tag:laptop"],
"dst": ["tag:server"],
"users": ["autogroup:nonroot"],
},
],
"tagOwners": {
"tag:server": ["username@github"],
"tag:phone": ["username@github"],
"tag:laptop": ["username@github"],
},
For each machine/device listed under the machines tab in the admin console I then assigned the ACL tags created via the telnet policy file to the relevant machine/device.
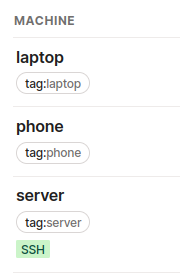
From my laptop I can then connect over tailscale SSH:
When you enable Tailscale SSH, Tailscale claims port 22 for the Tailscale IP address (that is, only for traffic coming from your tailnet) on the devices for which you have enabled Tailscale SSH. This routes SSH traffic for the device from the Tailscale network to an SSH server run by Tailscale, instead of your standard SSH server.
sudo tailscale up
ssh simon@server
Or via my phone using an SSH client (ie. connectbot):
You can read here how tailscale is different from SSH
Other benefits to explore:
- Remove SSH access from my linux servers firewall and stop sshd running altogether
- Running services on local ports and access them directly from any connected device
- Share files easily between machines via taildrop
- Check out using a private short link service for a tailnet
Simons blog / 2022 / 12 / 20